Ticker
How Do Ethical Hacker Can Earn? Beginner Guide
Ethical hacking also known as White hat hacking is a best practice of computer security skills and the purpose of securing companies as well as organ…
Continue ReadingScrap WhatsApp Group Members Details In CSV Format For Free
In this digital era, everyone needs leads from their targeted audience and actually, they are buying data from others. What happens if you can scrap …
Continue ReadingZoom Found Critical Vulnerabilities Let Attackers Escalate Privileges ! Update Now
Zoom Video Communications has uncovered a few basic vulnerabilities influencing its Work environment Apps, SDKs, and Rooms Clients. These vulnerabili…
Continue ReadingHow to use Toutatis to extract information from Instagram accounts
In this article we will learn how to extract information such as email id , phone no , profile picture from Instagram account. Toutatis is a speciali…
Continue ReadingGuide to Android Penetration Testing for Beginners
Our mobile apps and services are a big part of our daily lives, which makes them a popular target for hackers trying to steal sensitive information. …
Continue ReadingKali Net-Hunter Complete Guide for Beginners
Are you interested in using Kali NetHunter but don’t know where to start? You’ve come to the right place. In the field of ethical hacking and penetra…
Continue ReadingActual Virtual Machine Software For Android To Run Different Computer Operating Systems
You probably know some ways to temporarily or permanently different computer-based operating systems on Android smartphones by using remote software …
Continue ReadingHow To Bypass Device Verification For Gmail Account | Lost Device Email Recovery
This guide is intended to help people who may have lost access to their device and need to log in to their Gmail account. Please note that this inf…
Continue ReadingA Bluetooth Control Script for DDOS Bluetooth Devices Using L2Ping Of Death
Before starting this guide, can you name any smart device without Bluetooth integration? It's highly unlikely, as Bluetooth is the most commonly …
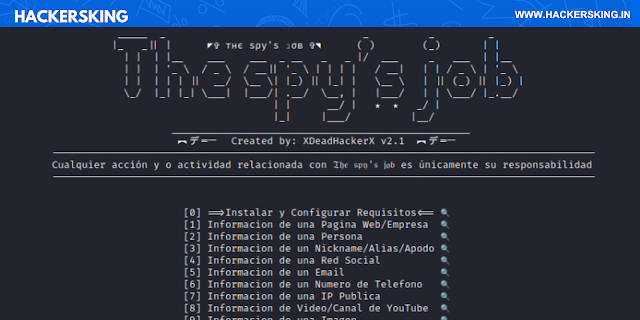
Continue ReadingThe Spy Job | All in one OSINT tool for Kali Linux
Open Source Intelligence (OSINT) is the act of gathering and analyzing publicly available data for research purposes, It is also the first stage of t…
Continue ReadingPopular Posts

Janitor AI: What is a Proxy and Why Should it Matter

How To Use Remote Access Trojan AndroRAT | All Errors Solved

Bypass Screenshot Restriction in Apps Without Root
Labels
YouTube
About us
Tech consumers look to Hackersking for the latest Ethical Hacking & Cyber Security guides, News, Technology tips & tricks.
admin@hackersking.com
Important Links
Copyright (c) 2025 Hackersking All Rights Reserved