Ticker
Phishing Attack Through WinRAR File Archiver Simulation Using .Zip Domain
In May 2023, Google released several new top-level domains (TLDs), including .dad, .phd, .mov, and .zip. Many cybersecurity communities began posting…
Continue ReadingAll-In-One Free Video Downloader For Desktop Use
Not everyone uses mobiles to scroll reels, watch tutorials, or view their favorite videos. Instead, a lot of people prefer large screens to enjoy an …
Continue ReadingPermissionless Mic & Camera Access Using Chromium Browser
In this blog, we discuss a new type of phishing attack where the victim doesn't even need to grant permission to access their camera, microphone,…
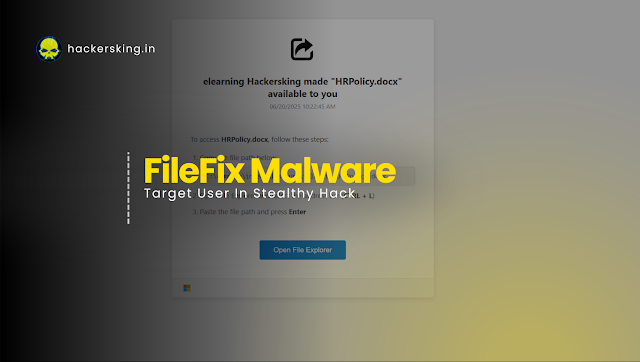
Continue ReadingNew Malware FileFix That Exploits File Explorer to Execute PowerShell Commands
What if we told you that simply copying and pasting a file path into your File Explorer could allow a hacker to run commands on your computer without…
Continue ReadingPuter The Internet OS! Free, Open-Source, and Self-Hostable
In an era where cloud computing and remote work are becoming the norm, the need for accessible, secure, and customizable digital environments has nev…
Continue ReadingOpen Source Tool For Activating Microsoft Windows and Office
The struggle to activate Windows or Microsoft Office is surely a problem many face. The annoyance of the endless “ Activate Windows ” watermark or th…
Continue ReadingVenator Browser For Ethical Hackers and Cybersecurity Researchers
As an ethical hacker or cybersecurity researcher, when you need to breach or analyze a target, you often have to explore various websites for distinc…
Continue ReadingHow To Use Remote Access Trojan AndroRAT | All Errors Solved
AndroRAT, or Android Remote Administration Tool, is a free software that allows someone to control an Android device remotely. It was initially creat…
Continue ReadingA Open-Source Multiboot USB Solution Ventoy
When it comes to bootable USB tools, Ventoy stands out as an amazing open-source solution that makes creating multiboot USB drives a breeze! Develope…
Continue ReadingApktool 2.11.1 Latest Version Complete Installation Guide On Linux
Whether you're an ethical hacker, a cybersecurity enthusiast, or a developer looking to modify an APK, Apktool is your first essential tool for …
Continue ReadingPopular Posts
Labels
YouTube
About us
Tech consumers look to Hackersking for the latest Ethical Hacking & Cyber Security guides, News, Technology tips & tricks.
admin@hackersking.com
Important Links
Copyright (c) 2025 Hackersking All Rights Reserved