Ticker
How To Delete An Instagram Fake Account
Instagram is a widely and the fastest growing online social media platform by Meta and daily thousands of accounts are created and deleted on Instagr…
Continue ReadingBrowser In The Browser Phishing Attack With Example
We recently researched a new type of phishing technique that targets a wider range of users' account all over the world and give instant access t…
Continue ReadingHTTrack for clone almost any webiste complete source code
Hello everyone I'm back with another topic of social engineering which is widely used by hackers/attackers using a tool known as HTTrack . So hop…
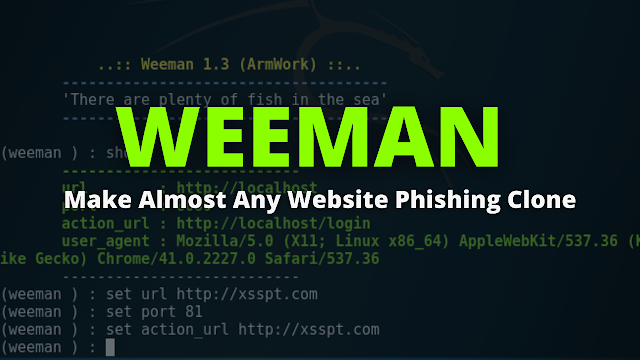
Continue ReadingWeeman Framework For Website Cloning | Linux & Termux
Hello Hacker/Pen-Testers, I am back with another post in which I introduce you to a tool that can clone almost any website page and host it on a LAN/…
Continue ReadingWishFish v3.0 All Error Fixes And New Features Added | Latest Update 2022
Everyone message or mailing me about WishFish Ngrok Error in which user not able to generate any URL and if somehow manage to get Ngrok URL then it s…
Continue ReadingHide Phishing URL Under A Normal Looking URL Using Maskphish Tool
Hello viewers I come back with another exciting tutorial in which we going to show you how hackers mask phishing URLs under a normal looking URL usi…
Continue ReadingGenerate IDN Homographic URL For Advance Phising Attack
People today are smarter than ever before, and since everyone is aware of phishing attacks, it is very difficult for hackers or attackers to trick…
Continue ReadingHow To Make Permanent Phishing Site For Lifetime Free
Hey guys we are come back with another excited topic in which we are going to show you how to make a permanent phishing site for completely free of …
Continue ReadingFlux-Keylogger Modern JavaScript Kelogger With Web Panel
So hey guys we are come back with another excited ethical hacking & cyber security blog post in which we are going to introduce you with the po…
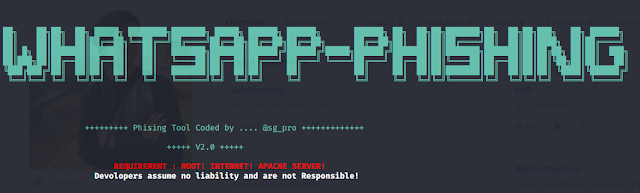
Continue ReadingMake Access On WhatsApp Accounts With Phishing Attack !
Now-day's whatsapp is the one of top ranking social media around the world and everyone use it and we also know whatsapp have end to end encryp…
Continue ReadingMost Complete Pentesting Toolkit For - Tools Hacker v2.0
Hey guys we are come back with another ethical hacking post in which we are going to introduce you with the most complete pentesting or hacking too…
Continue ReadingWishFish v2.0 - Host Custom Pages (Errors Fixed)
Hey guys we are come back with another excited tutorial in which we are going to introduce you with the latest and updated version WishFish v2.0 t…
Continue ReadingBypass Or Steal Login OTP Using Phishing Attack
Hello and welcome back friends we are come back with another excited tutorial in which we are going to show you how login OTP (One Time Password) ca…
Continue ReadingAccess Any Android Mic Using A Phishing Link : No Trojan 2024 Updated
We covered different social engineering techniques in this blog in which we learned how an attacker gains access to a victim's sensitive informat…
Continue ReadingPopular Posts

Janitor AI: What is a Proxy and Why Should it Matter

How To Use Remote Access Trojan AndroRAT | All Errors Solved

How To Install Kali NetHunter Lite On Any Android Device
Labels
YouTube
About us
Tech consumers look to Hackersking for the latest Ethical Hacking & Cyber Security guides, News, Technology tips & tricks.
admin@hackersking.com
Important Links
Copyright (c) 2025 Hackersking All Rights Reserved